
In the fast-evolving world of cryptocurrencies, fraudsters are continuously devising new methods to exploit unsuspecting individuals. One such scheme gaining traction is the Multi-Signature 'Fish Farming' scam. This article aims to shed light on this fraudulent activity, providing insights into the methods used, explaining the concept of multisig wallets, discussing other forms of wallet fraud, and offering practical tips to avoid falling victim to phishing scams.
I. Methods of Fraud:
The Multi-Signature 'Fish Farming' scam typically initiates with an innocent plea for help on popular platforms such as Twitter or Telegram. Victims receive messages along the lines of, "I have 100/1,000 USDT in my wallet, but I am unable to withdraw it. If you can assist me, you'll be rewarded with some USDT." Intrigued, individuals respond with the intention of aiding newcomers to the world of Web3 wallets. However, upon importing the wallet using the provided private key or mnemonic phrase, victims discover that although the balance is displayed, the assets cannot be withdrawn.
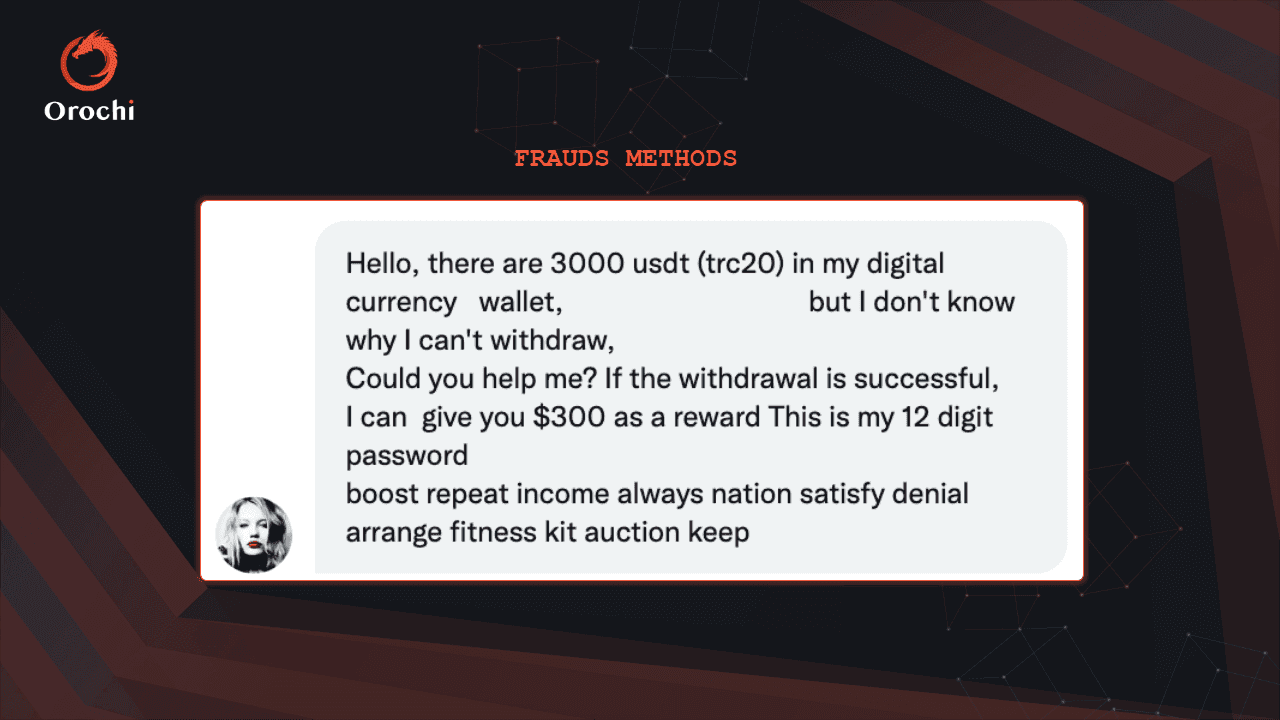
The scammers then inform the victims that a commission fee, usually around USD 10, needs to be deposited to enable the withdrawal. Unfortunately, even after making the deposit, the assets remain inaccessible. It becomes evident that this was an elaborate fraud, exploiting people's kindness or greed. The scammers employ various excuses to manipulate victims, dissuading them from pursuing the matter further, while actively seeking their next target. As long as there are enough victims, these criminals stand to make substantial profits.
II. Explanation with Multisig Wallets:
To comprehend why assets cannot be withdrawn after importing a private key, it is essential to understand multisig (multi-signature) wallets. Before delving into multisig wallets, let us first explore single-signature wallets, which are the standard choice for most investors. In a single-signature wallet, a signature from the wallet owner is sufficient to execute a transaction and successfully transfer funds to the blockchain.

In contrast, multisig wallets require multiple signatures to complete a transaction. These wallets can be configured in various ways, depending on the desired security level.
For instance, a 1/2 multisig mode enables two individuals or a single person with two wallets to independently initiate transactions.
In a 2/2 multisig mode, both administrators must consent to the transfer using their respective private keys.
Similarly, a 2/3 multisig mode is suitable for funds jointly managed by three partners, requiring the authorization of two private keys to execute a transaction.
Scammers exploit the inherent nature of multisig wallets in this fraud. They create a multisig wallet, deposit some USDT as bait, and then establish communication with potential victims in community forums or direct messages. By gaining the victims' trust and sharing the private key and mnemonic phrase, they convince victims to make a deposit. However, since transfers from a multisig wallet necessitate multiple private keys, victims find themselves unable to withdraw any assets.
III. Some other forms of wallet fraud that you should know:
To further enhance your awareness of wallet fraud in the cryptocurrency space, here are some common forms of fraudulent activities you should be familiar with:
1. Phishing attacks: Scammers employ phishing techniques by posing as legitimate entities and tricking individuals into revealing sensitive information like private keys, passwords, or personal data. Be cautious of unsolicited messages and double-check the authenticity of the source before sharing any confidential details.
**2. Fake wallets and apps: **Fraudsters create deceptive wallets or mobile applications that mimic legitimate ones. These fake tools are designed to steal private keys and sensitive information, giving scammers access to your digital assets. Prioritize using well-established wallets and applications from trusted sources.
3. Ponzi schemes: Ponzi schemes promise high returns on investments but operate by using funds from new investors to pay earlier participants. These fraudulent schemes eventually collapse, leaving unsuspecting individuals at a loss. Be skeptical of unrealistic promises and conduct thorough research before investing your funds.
**4. Social engineering tactics: **Scammers exploit human psychology to manipulate individuals into divulging confidential information or performing unintended actions. They may impersonate authority figures, friends, or acquaintances to gain your trust. Exercise caution and verify the legitimacy of any requests before taking action.
By familiarizing yourself with these various forms of wallet fraud, you can better protect yourself and your digital assets from potential threats.
IV. How to avoid phishing frauds:
Protecting oneself from wallet fraud, including phishing scams, requires a combination of vigilance and best practices. Here are some essential tips to avoid falling victim to these fraudulent activities:
1. Exercise caution and skepticism: Be wary of unsolicited messages or requests for personal information and funds. Verify the legitimacy of the source and never share sensitive details impulsively.
2. Double-check website URLs: When accessing cryptocurrency platforms or wallets, ensure the website's URL is correct and secure. Look for "https" and a padlock icon to indicate a secure connection.
3. Utilize reputable wallets: Stick to well-known wallets and applications from trusted sources. Research and read reviews before downloading or using any cryptocurrency-related software.
**4. Keep software up to date: **Regularly update your wallet software, applications, and operating system to benefit from the latest security patches and bug fixes.
5. Educate yourself: Stay informed about common scams and fraud tactics prevalent in the cryptocurrency space. Knowledge is a powerful tool in protecting yourself from potential threats.
In terms of security, users can avoid scam events if they have enough knowledge and protect themselves, in addition, you can also use products that upgrade and increase security cryptography like Multisigs wallet.
Multi Signature wallets like Orosign can provide an additional layer of security against hackers. Multisig wallets require two or more private keys to authorize a transaction, making it much harder for hackers to gain access to your funds. In addition, Orosign is completely open to support payments/escrows for e-commerce platforms.
Orosign is a Self-Managing Mobile App For Digital Assets that serves as an interface of Orochi Ecosystem, which can integrate multiple games and native decentralized applications. Orosign allows users to interact with all applications on Orochi Computation Layer and empowers customers to organize and manage their digital assets.
Orosign is designed for ease of use, even for non-crypto users. You can send, receive or store various cryptocurrencies and digital assets safely and securely with Orosign mobile app.
Currently, Orosign allows customers to create their own multisignature wallet with minimal cost as well as customize smart contracts to meet their own expectations. Off-chain signing and verification are used to secure the signing process. All proofs are verified independently with secp256k1, which is the most widely used elliptic curve in the blockchain space, thanks to its 256 bits security level. Thus, the fund is safe as long as the majority of private keys are safe
Read more about why should we own a Multisignature Wallet?
Read more about Orosign
Conclusions:
As cryptocurrencies continue to gain prominence, the risk of wallet fraud and scams also increases. Understanding the methods employed by fraudsters, such as the Multi-Signature 'Fish Farming' scam, is crucial to safeguarding your digital assets. By familiarizing oneself with the concept of multisig wallets, recognizing other forms of wallet fraud, and adopting preventive measures, individuals can navigate the cryptocurrency landscape with greater confidence and security. Stay informed, exercise caution, and protect your digital wealth from those seeking to exploit it.
Experience verifiable data in action - Join the zkDatabase live demo!
Book a Demo











