The Ultimate Guide to Understanding Multisignature Wallet
November 4, 2025
10 mins read
Multisig stands for “multi-signature”, a specific kind of digital signature that enables two or more people to sign documents collectively. As a result, a multi-signature is created by fusing several distinct signatures

Multisig stands for “multi-signature”, a specific kind of digital signature that enables two or more people to sign documents** **collectively. As a result, a multi-signature is created by fusing several distinct signatures. Although multisig addresses may be utilized in various circumstances, the majority of use cases are tied to security issues.
From a security standpoint, coins and tokens must be stored in a way that completely removes the risk associated with a single weak point that might compromise the entire wallet. If only one private key is required to sign a transaction, your assets are at serious risk of being stolen or lost.
In order to minimize this issue, it is wisely recommended to use a wallet that requires more than one private key for transaction authorization. Sometimes it takes two, three, or even more private keys from various sources to sign a transaction. Many blockchains allow for the construction of multisignature addresses, and exchanges and wallet providers use some variation of a multisignature wallet to protect their customers' money.
Multisignature Wallet Characteristics:
-
A multisignature wallet requires more than one private key to authenticate crypto transactions
-
They can also be set up to enable the generation of signatures from each of the set's private keys.
-
Private keys should be kept in separate places to boost security, while improving usability by allowing multiple keys to sign a transaction.
Types of MultiSig wallets:
-
n-of-n: All keys are required to authorize a transaction. (2-of-2, 3-of-3, etc.)
-
n-of-m: Some of the keys are required to authorize a transaction, not necessarily all of them. (1-of-2, 2-of-3, 3-of-4, etc.)
Fundamentals of Multisignature Wallets
Commonly, you only need one private key to authorize a transaction on a blockchain. However, there are a lot of blockchains that allow users to create multisignature addresses that require more than one private key to sign a transaction. Only the keys listed in the address can be utilized (e.g., yours, your friend and your security company’s key in a 3-of-3 wallet).
There are different combinations with various usage exists of multisignature wallets such as 2-of-2, 3-of-3, 2-of-3 or 1-of-2. A signature cannot be generated or the transaction authorized unless the necessary number of private keys are utilized. This indicates that, for the most part, even if one of the keys is stolen, your funds will still be protected.
Multisignature Wallets Types
Cryptocurrency wallets with multiple signatures can be identified by the number of active private keys and the number of signatures needed to approve a transaction. Here are a few settings that are frequently used on cryptocurrency exchanges as well as in personal wallets.
1-of-2 Multisig Wallet
Many users can share funds via multisignature wallets. If you wish to share access to funds in a single wallet with a reliable individual, you can configure a wallet such that any of your two keys can sign documents. Nevertheless, neither key is required, so you can each use the money on your own.
2-of-2 Multisig Wallet
The 2-of-2 multisignature technique is used in wallets secured by the two-factor authentication (2FA) feature. The goal is to store private keys on two different gadgets. As an illustration, one private key might be kept on a computer and the other on a portable device. No transaction can be approved without both devices signing it. The 2-of-2 multisignature wallet boosts security, but comes with the chance that you won't be able to access your money if one of the devices is compromised.
2-of-3 Multisig Wallet
This particular type of multisignature wallet needs two out of the three active private keys to approve transactions. Exchanges frequently employ them to increase the security of their hot wallets. One private key is kept online by an exchange that supports 2-of-3 multisignature addresses, and the other is kept offline on a separate device, while a security firm stores the third secret key. Private keys are held by two different organizations, so even if one of them is compromised, the wallet is still secure. In the event that the security partner goes out of business, the offline backup key further secures the hot wallet.
How Does a Multisignature Wallet Work?
The fundamental steps for using a multisignature wallet remain the same regardless of how many key holders you have. When one user chooses to use their wallet to conduct a transaction, the process begins. They insert the transaction's specifics into their wallet and sign the transaction with their key. However, the deal hasn't been sealed yet. The transaction won't be finalized until all necessary keys have been signed. When the right amount of keys have been input, the wallet automatically signs the transaction and sends the money to the correct address.
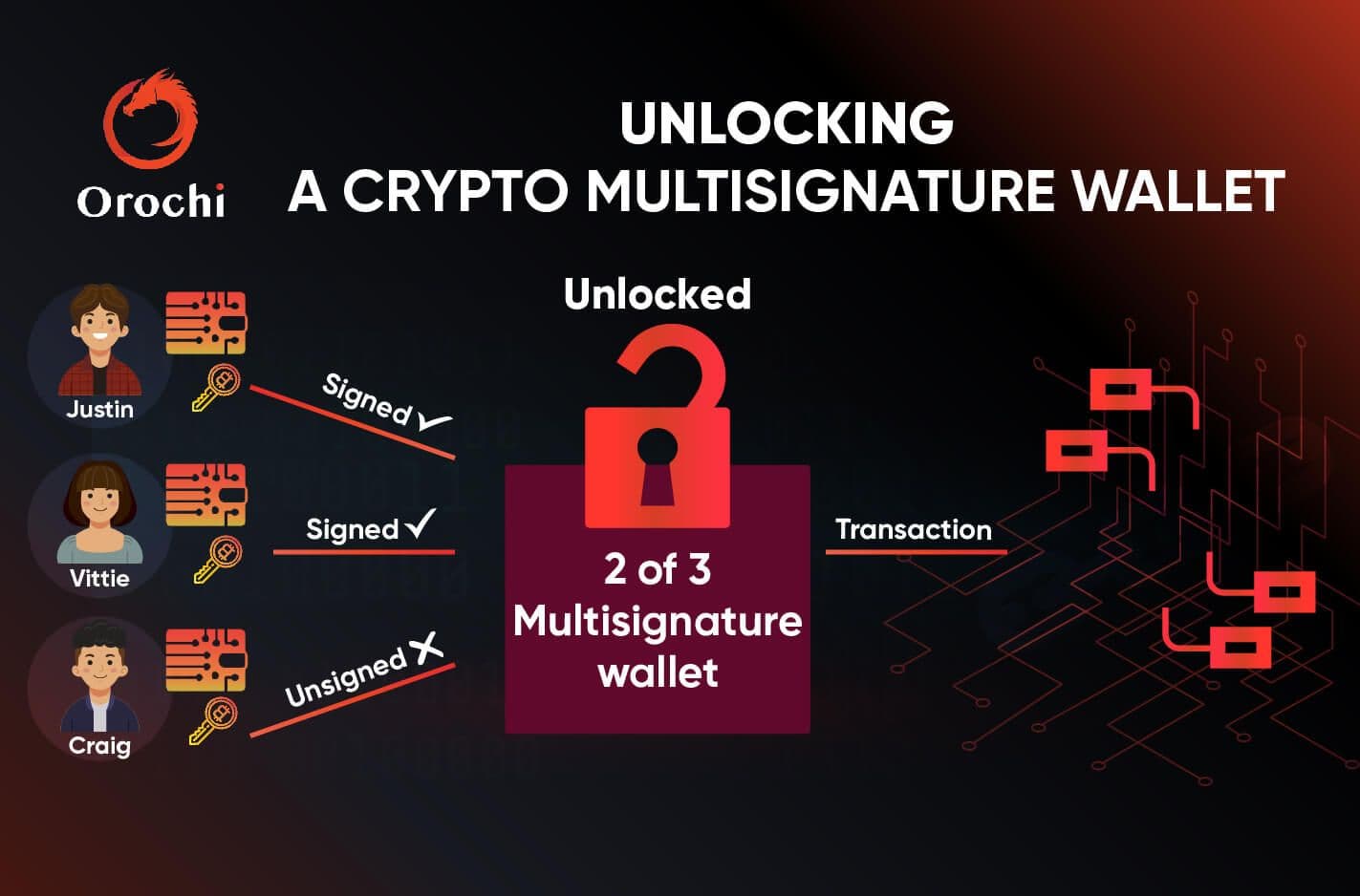
There is no hierarchy in multisignature wallets. For instance, if a transaction needs to be validated by four out of five private keys in the multisignature wallet, no specific signature is required to complete the transaction. Instead, any four out of the five users are free to sign the transaction in any order they want. The transactions never run out. Pending transaction proposals won't be finished until all necessary signatures are provided.
Use Cases of Multisignature Cryptocurrency Wallets
Increasing Security
Users are able to avoid the issues brought on by the loss or theft of a private key by using a multisignature wallet. The money is therefore secure even if one of the keys is stolen. Consider a scenario where you generate a 2-of-3 multisignature address and save each private key on a different device or location (e.g. mobile phone, laptop, and tablet). In case your laptop is stolen, the thief won’t be able to access your money with just one of the three keys. In a similar scenario, if the hacker conducts malware infections or phishing attacks to your wallet, it is less likely to be successful because he would most likely only have access to one device and key.
Despite malicious attempts, you can still access your money if you misplace one of your private keys by utilizing the other two.
Two-factor Authentication
You can construct a two-factor authentication system to access your funds by creating a multisignature wallet that needs two keys. You might, for instance, maintain one private key on your laptop and the other on your phone. This would guarantee that a transaction could only be completed by someone who has access to both keys. But be aware that utilizing multisignature as a two-factor authentication method can be risky, especially if it is configured as a 2-of-2 multisignature address. You won't have access to your money if one of the keys is stolen. Hence, using a 2-of-3 multisig address setup would be safer.
Escrow Transactions
Having a 2-of-3 multisignature wallet can facilitate an escrow transaction between two parties (you and your friend, for example) that includes a third party serving as a mutually trusted arbiter in case something happens unexpectedly.
In this case, you would deposit the money first, and it would be secured (neither user being able to access them on their own). Then you and your friend can both use their keys to sign and conclude the deal if your friend delivers the products or services as agreed upon.
The only case that the third party (the arbiter) would have to intervene is if there is a dispute, at which point he could use his key to generate a signature and give it to either you or your friend, depending on the arbiter’s judgment.
Decentralized Decision Making
A multisignature wallet may be used by the board of directors to regulate who has access to a company's funds. No single board member can misuse the cash, for instance, by establishing a 4-of-6 wallet where each member has a key. As a result, only judgments supported by the majority can be put into action.
Can a multisig wallet be used to commit a scam?
Yes, scammers can use a multisig wallet to deceive the victim.
For example:
-
The victim buys cryptocurrency, probably at a deal that seems too good to be true.
-
The money is transferred to a multisig wallet that the victim has access to but does not own. In order to move the money without the victim's permission, the attacker might, for instance, set up a 1-2 multisig wallet.
-
The money is transferred by the attackers to a wallet that the victim cannot access.
Our recommendations:
-
If you are buying cryptocurrency, please ensure that the wallet you will use to receive the money is one that you own, one that you have created, one that isn't multisig, and one that only you have access to.
-
If you're buying cryptocurrencies, watch out for "too good to be true" pricing or anyone offering it for a lot less than its current value.
Q&A
Q: Is Orosign a multisig wallet?
A: Orosign is a Self-Managing Mobile App For Digital Assets that serves as an interface of Orochi Ecosystem. You can create a multisig wallet using Orosign.
Q: I want to increase the security of my money. Would a multisig wallet be a suitable choice?
A: A multisig wallet increases the security of your wallet by requiring multiple signatures to sign a transaction. If you demand at least two signatures, even if an attacker got their hands on one copayer's device, they wouldn't be able to use the money in your wallet. However, bear the following in mind:
-
Every time you want to sign a transaction, it requires signature from the required number of copayers
-
You'll need several recovery phrases in order to get your wallet back.
Q: I want to share a wallet with my friend, what do you recommend:
A: There are lots of multisig wallet types for two copayers:
-
1 of 2: A single signature is all that is necessary to sign a transaction. A proposal does not require the signature of either of the copayers. With just one recovery phrase, the wallet can be recovered
-
2 of 2: To send a transaction, two signatures are needed. A copayer must wait for the other copayer's approval before creating a transaction proposal. Two recovery phrases are necessary in this wallet arrangement in order to restore the wallet. The wallet and cash are lost if one device is lost or stolen and you do not have that copayer's recovery phrase.
-
2 of 3: Two signatures and three copayers are necessary. When there is a chance of losing one of the devices, this wallet design emerges as a good choice because it includes an additional recovery phrase that is safely stored independently. Additionally, 2-4 might be a wise choice.
Q: I own a 2 of 2 wallet. The other copayer's device has been lost, and they are also missing their recovery phrase. How can we get the wallet back?
**A: **Sadly, there is no way to get the wallet back in this situation. The wallet must be recovered using both recovery phrases.
Q: I own a 2 of 2 wallet. I have my wallet set up in two devices, but the other copayer has lost their device and does not have their recovery phrase. Why can't I transfer money?
**A: **To transfer payments, a different and distinctive signature from each copayer is required. This means that using several copies of the same copayer wallet does not help because they both provide the same signature. If you misplace any recovery phrases for a multisig wallet (such as 2-2), you will no longer be able to access the wallet's money.
Experience verifiable data in action - Join the zkDatabase live demo!
Book a Demo











