
Data Provenance and Integrity in Tokenized Markets is essential for building trust in Web3 and DeFi ecosystems. As enterprises and developers scale Real-World Asset Tokenization (RWA Tokenization), the authenticity, lineage, and verifiability of every datum—from price feeds to asset records—become decisive. When inputs are unverifiable or privacy-hostile, AI models drift, RWA mints misprice, and DePIN sensors can be spoofed. The result is stalled adoption and regulatory pushback.
Orochi Network provides a proof-agnostic Verifiable Data Infrastructure designed for APAC and US markets: 300,000+ daily users, 1.5M+ monthly users, 160M+ total transactions, 40+ dApps, zkDatabase spanning 20+ chains, and Orand/Orocle integrated across 49+ chains. Its ZK-based stack delivers audit-grade proofs, recursive compression, and privacy-preserving data flows—foundational for RWA scale with lower costs and stronger compliance.
The Problem: Unverified, Privacy-Leaking Inputs
Tokenized markets fundamentally rely on Data Provenance and Integrity in Tokenized Markets. Yet most pipelines still depend on unverifiable off-chain data, manual reconciliation, and non-attested feeds:
- Mispricing & NAV drift: Without verifiable data provenance, yields and collateral values become unreliable.
- Compliance degradation: Regulators require integrity in tokenized markets; screenshots and manual logs are not audit trails.
- AI contamination: AI models incorporating unverified inputs lose regulatory auditability.
- DePIN spoofing: Without data provenance in IoT, sensors can falsify locations, corrupting rewards.
- High verification costs: Lack of recursive ZK pipelines leads to expensive L1 verification and poor integrity guarantees.
Current Market Snapshot: Why RWA Needs Verifiable, Private Data Now
RWA entered the industrial phase in 2025, making Data Provenance and Integrity in Tokenized Markets a non-negotiable requirement:
- Market size: Tokenized RWAs crossed $30B in Q3 2025; treasuries ($7.3B) and private credit (~$17B) dominate; commodities and tokenized funds each ~ $2B.

- Growth trajectory: RWAs expanded ~10x from ~$2.9B in 2022 to >$30B by Oct 2025; U.S. treasuries rose to ~$8.7–$8.8B by end-Oct 2025; private credit surpassed ~$17–$18.7B.

- Rails and venues: Provenance and Ethereum host the largest public volumes; permissioned networks like Canton process multi-trillion settlement flows monthly; stablecoins increasingly act as cash-equivalent collateral and settlement assets.
- Policy momentum: U.S. (GENIUS Act; SEC Project Crypto), UK (Digital Securities Sandbox), Singapore/Japan/HK/Australia pilots and licensing signals; alignment around “same activity, same risk, same regulatory outcome.
Why Does Data Provenance Matter in Tokenized Markets?
Data Provenance and Integrity in Tokenized Markets ensures every asset, price feed, transaction, and collateral entry is cryptographically traceable—from real-world origin to on-chain representation.
In RWA Tokenization, it provides a verifiable chain from physical or financial assets to on-chain representations. Provenance ensures that token holders, regulators, and auditors can trust the underlying assets, crucial for institutional adoption.
As tokenized markets scale to billions and move into regulated environments, the most critical requirement is provable and privacy-preserving data inputs. Without Data Provenance and Integrity in Tokenized Markets, tokenization frameworks become vulnerable to mispricing, oracle drift, spoofed data, and compliance failur
Without robust provenance:
- Mispriced assets may propagate through DeFi protocols, risking financial loss.
- AI models used for pricing or risk analysis may operate on corrupted data.
- Regulatory scrutiny can halt tokenization initiatives, delaying market entry.
Orochi Network addresses these risks using a ZKP based Verifiable Data Pipeline. Each transformation and query generates a cryptographic proof, ensuring that data integrity is auditable and tamper-resistant.
This framework is particularly critical for Real-World Asset Tokenization (RWA Tokenization), where data authenticity directly correlates to market trust and compliance.
How Does Blockchain Help Protect Data Integrity?
Blockchain technology enforces immutability and distributed consensus, creating a ledger where each transaction is verifiable and permanent. In tokenized markets, blockchain ensures that once asset data or transactions are recorded, they cannot be altered retroactively without detection.
Blockchain adds immutable audit trails, ensuring Data Provenance and Integrity in Tokenized Markets remains intact:
- Transparent recording of tokenized asset transfers.
- Immutable audit trails for regulators and institutional stakeholders.
- Integration with smart contracts for automated enforcement of compliance and business logic.
By combining blockchain immutability with verifiable data proofs, enterprises can assure stakeholders that tokenized assets accurately mirror their real-world counterparts.
How Do Zero-Knowledge Proofs Make Data Safer?
Zero-Knowledge Proofs (ZKPs) allow verification of data correctness without revealing the underlying information. Advanced ZK systems, Halo2, zk-STARK, Plonky3, and recursive proofs, enable secure, scalable verification across millions of data points.
For instance, Orochi’s ZK-data-Rollups reduce verification costs from ~$25 to ~$0.002/KB while preserving privacy, an essential requirement for Data Provenance and Integrity in Tokenized Markets, where institutions must verify everything without exposing PII or contractual terms.
How Does Verifiable Data Infrastructure Transform Tokenized Markets?
A Verifiable Data Infrastructure ensures that all data used for RWA Tokenization, DePIN, or AI analytics is provable, tamper-resistant, and auditable. By embedding verifiability into data pipelines, enterprises can adopt tokenization with confidence, meeting regulatory requirements and market expectations.
Orochi Network exemplifies this transformation in APAC and US markets, supporting secure, multi-chain tokenization while enabling cost-efficient, privacy-preserving proofs.
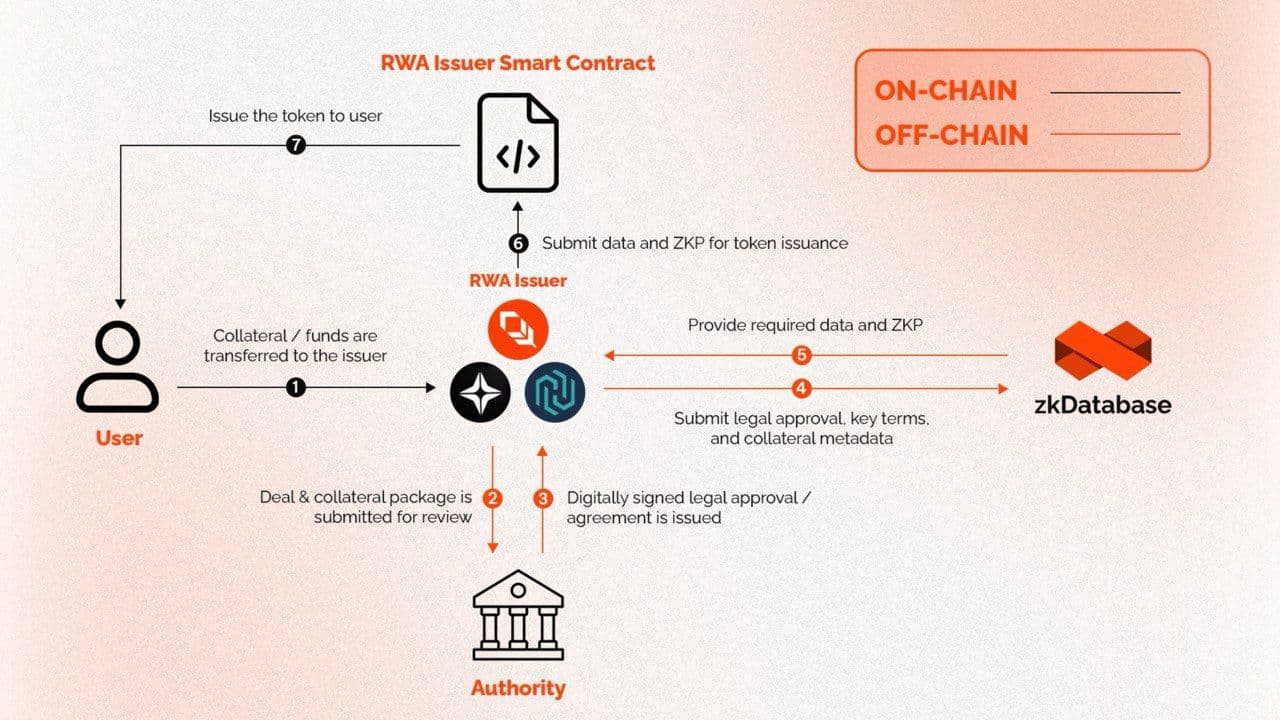
What Are the Key Components of Orochi’s Infrastructure?
- zkDatabase: A provable database that supports multi-chain integration (20+ blockchains) and recursive proof generation. It delivers low-latency verification (~500ms) for millions of operations.
- Orand: Provides verifiable randomness across 120+ chains, using deterministic cryptography to prevent manipulation.
- Orocle: A decentralized oracle service that securely bridges off-chain data to on-chain environments, addressing the Oracle Problem in Tokenized Markets by batching, rotating storage, and generating verifiable random functions.
What’s the implication?
Institutional adoption is converging on fixed income, MMFs, and credit, segments that demand precise provenance, privacy-preserving verification, and audit-grade integrity. Verifiable data is no longer optional; it’s a market gate.
Market Challenges Blocking Scale:
- Fragmented data custody: Documents and records scattered across custodians without cryptographic attestations; reconciliation is manual and error-prone.
- Privacy vs. proof trade-offs: Institutions must prove correctness without exposing PII or deal terms; most stacks leak sensitive info in logs and indices.
- Cross-chain state risk: Multi-chain issuance and settlement create consistency problems when bridges and indexers lack provable state.
- Cost of verification: Naive on-chain checks can cost ~$20–$30 per submission; without batching/recursion, teams throttle verification frequency.
- Oracle reliability: Single-source or unverified feeds introduce manipulation risk; SLAs are often not enforced with verifiable evidence.
ZK Technology for Real-World Assets: Secure Proofs, Confidential Data
Zero-Knowledge Proofs (Halo2, zk-STARKs, Plonky3) and recursive composition let institutions verify correctness privately and cheaply:
- Confidential verification: Prove data correctness without exposing PII, document internals, or contractual terms.
- Cost compression: Batching + recursion can reduce verification from ~$25 to ~$0.002 per KB equivalent, enabling higher-frequency attestations.
- Cross-system integrity: Map proofs from off-chain systems (databases, ledgers) to on-chain commitments; enforce at read-time or write-time.
Verifiable Data Infrastructure: The Stack RWA Needs
Verifiable Data Infrastructure is the end-to-end system for attestation, proof generation, storage, and on-chain verification:
- Attest origin and transformations
- Prove query correctness and policy compliance
- Commit proofs on-chain for auditability
- Integrate with oracles and verifiable randomness for fair operations This is the operational backbone for APAC + US adoption where regulators and risk teams require evidence, not claims.
Case Studies
Mirror Protocol (May 2022): Multi-Million Synthetic Asset Exploit
In May 2022, Mirror Protocol experienced a high-profile failure that has remained a canonical example of risks in RWA-adjacent systems through 2024–2025. A misconfiguration between validators and oracles caused Terra Classic validators to report LUNA prices instead of LUNC, dramatically inflating asset valuations (~$9.8 vs ~$0.0001).

Attackers exploited this discrepancy to mint and liquidate synthetic assets, resulting in immediate losses exceeding $2 million, with an earlier, separate bug contributing over $30 million across hundreds of transactions.
The root cause was not merely a single bug but a stale, uncoordinated oracle pipeline. Synthetic asset systems and tokenized RWAs are highly dependent on accurate, timely data. Any lapse in data integrity—whether in reported NAVs, collateral values, or redemption metrics, can be catastrophically amplified, leading to mispricing, systemic risk, and financial loss.
**zkDatabase as a Solution:**
- Verifiable Data Pipelines: At each stage, zkDatabase enforces cryptographic proofs of validity, ensuring that prices, NAVs, and collateral values are provably accurate before they are used in synthetic asset operations.
- Immutable, Audit-Grade Records: Every data point is logged in a tamper-proof manner, providing full traceability for compliance and post-mortem analysis.
- Oracle-Proof Aggregation: By aggregating multiple data sources with zero-knowledge proofs, zkDatabase ensures that even if a node or validator reports stale or incorrect data, it cannot manipulate the resulting NAV or synthetic minting process.
In essence, zkDatabase eliminates the type of systemic exploit that Mirror Protocol experienced by guaranteeing that no unverified or misreported data can influence critical financial operations.
DePIN Hotspot Spoofing (Hong Kong, 2021–2022): Compromised IoT Provenance
Another instructive case comes from early DePIN trials in Hong Kong, 2021–2022, where falsified device locations distorted rewards and claimed coverage metrics. Field investigations revealed hotspots “witnessing” each other from implausible distances, earning disproportionate rewards (~$78 in two weeks vs ~$2 for genuine hotspots) without ever transferring real network data.
For tokenized infrastructure and IoT-backed RWAs, this represents a fundamental integrity problem: spoofed provenance corrupts utilization metrics, misguides demand signals, and distorts asset valuations tied to sensor performance. Fraudulent data undermines tokenomics, investor trust, and the real-world utility of the network.
**zkDatabase as a Solution:**
- Device-Level Verifiable Proofs: Each IoT device or hotspot submits cryptographically verifiable proofs of location and activity, ensuring the network can confirm genuine operation without exposing private data.
- Real-Time Integrity Validation: Only proven activity is counted toward rewards, network coverage, or RWA valuations, preventing any exploitation from spoofed sensors.
- Tamper-Proof Sensor Provenance Ledger: Provides auditable evidence for regulators, operators, and investors, creating accountability and traceability for all network data.
By integrating zkDatabase, DePIN networks and IoT-backed RWAs are shielded from fraudulent manipulation, ensuring that token issuance, rewards, and asset valuations reflect actual, verifiable real-world activity.
Conclusion
The tokenized market’s next phase depends on data provenance and integrity. With adoption surging across treasuries, MMFs, private credit, and real estate—and with APAC and US regulators converging on supervised, evidence-based models—organizations need verifiable, confidential data flows.
Orochi Network’s zkDatabase solves the core challenge: it proves data authenticity, lineage, and query correctness across 20+ chains, with recursive cost compression (~$25 → ~$0.002 per KB), millisecond-level proof generation, and seamless integration with Orand (verifiable randomness) and Orocle (verifiable oracle feeds across 49+ chains). For institutions and builders, zkDatabase is the fastest path to audit-grade trust, lower costs, and GEO-ready adoption in APAC and the US.
FAQs
Why is data provenance the core requirement for RWA tokenization?
Because tokenized assets inherit trust from their inputs. Provenance documents origin, movement, and transformations so regulators, auditors, and holders can verify asset backing. Without it, markets face mispricing, oracle drift, AI model contamination, and compliance failures, exactly the risks the Mirror Protocol incident exposed. Verifiable pipelines ensure each price, NAV, and eligibility check is cryptographically proven before on-chain use.
How does Orochi Network’s Verifiable Data Infrastructure improve security and cost?
Orochi’s zkDatabase, Orand, and Orocle generate proof-agnostic, audit-grade attestations across 20–49+ chains. Recursive ZK composition compresses verification from about $25 to ~$0.002 per KB, enabling high-frequency checks without leaking private data. The result is low-latency proofs, tamper-proof records, and resilient oracle aggregation for APAC and US deployments.
What’s the best practice for on-chain and off-chain data verification in RWA?
Attest origin, prove transformations and queries, then commit proofs on-chain. Use decentralized oracles with batching and storage rotation, pair with verifiable randomness to prevent manipulation, and enforce read-time or write-time checks in smart contracts. This closes the Oracle Problem in Tokenized Markets and aligns with Compliance and Regulation in Tokenization expectations.
Experience verifiable data in action - Join the zkDatabase live demo!
Book a Demo











